Regin’s architecture
In movies it sometimes seems like computer viruses are capable of doing anything. More often than not that’s a matter of dramatic license, but a recently discovered piece of complex malware suggests that truth may actually be scarier than fiction.
“Regin” is an extremely sophisticated piece of software—so sophisticated, in fact, that its discoverer, security firm Symantec, concludes that it can only be “one of the main cyberespionage tools used by a nation state.” In that sense, it compares most closely to Stuxnet, the software widely thought to be developed by Israel and the U.S. to infect machines involved in Iran’s nuclear program.
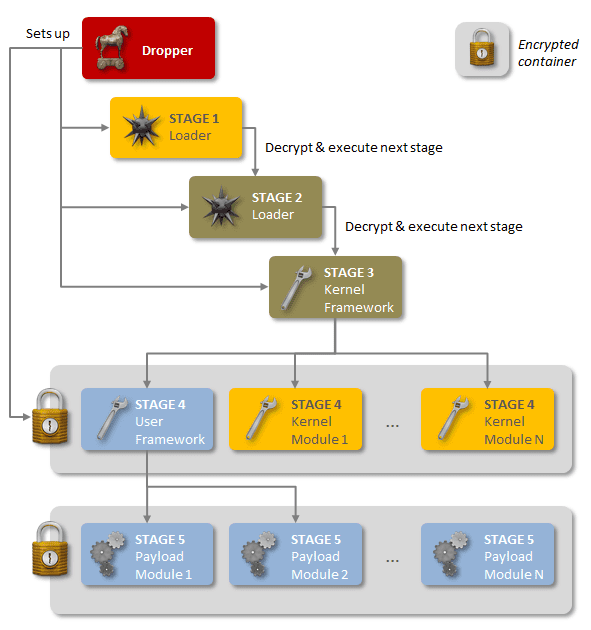
But Regin—which Symantec started studying in 2013, but believes has been in use since as far back as 2008—has a portfolio that’s much, much broader than that of Stuxnet. It’s wide-reaching and modular, with a variety of functions that can be loaded on demand to do things like steal passwords, capture screenshots, monitor network traffic, recover deleted files, and more. It’s unclear exactly how computers are infected, but Symantec’s research suggests Regin can use a variety of vectors, including fake versions of popular websites, instant messenger apps, and more. (The company has yet to find a vector used one more than once.)
What makes Regin so insidious is that it is incredibly stealthy, carefully cleaning up its tracks as it goes. Its files are strongly encrypted—the creators went so far as to create a virtual file system to store much of the data—and broken down into smaller chunks that are loaded sequentially. And the creators of the code can remotely decide which spying capabilities are needed for a particular target and deploy only that code.
Symantec’s analysis of Regin concludes that it’s clearly designed for long-term intelligence gathering. The malware seems to have infected a variety of targets, a significant chunk of which includes telecoms and other infrastructures, as well as private individuals and small businesses, but it’s also affected government organizations and research institutes. Infected computers have been found in ten countries thus far, with the biggest chunks in the Russian Federation and Saudi Arabia, as well as Mexico, Ireland, India, Afghanistan, Iran, and more.
The complexity of Regin is just another sign that we’ve reached an era where cyberespionage and cyberwarfare is happening around us all the time, just below the surface, and all without our knowledge.