At 8 a.m. on May 4, 2001, anyone trying to access the White House Web site got an error message. By noon, whitehouse.gov was down entirely, the victim of a so-called distributed denial-of-service (DDoS) attack. Somewhere in the world, hackers were pinging White House servers with thousands of page requests per second, clogging the site. Also attacked were sites for the U.S. Navy and various other federal departments.
A series of defacements left little doubt about where the attack originated. “Beat down Imperialism of American [sic]! Attack anti-Chinese arrogance!” read the Interior Department’s National Business Center site. “CHINA HACK!” proclaimed the Department of Labor home page. “I AM CHINESE,” declared a U.S. Navy page. By then, hackers from Saudi Arabia, Argentina and India had joined in. The military escalated its Infocon threat level from normal to alpha, indicating risk of crippling cyber-attack. Over the next few weeks, the White House site went down twice more. By the time the offensive was over, Chinese hackers had felled 1,000 American sites.
The cyber-conflict grew out of real-world tensions. A month earlier, a U.S. EP-3 reconnaissance aircraft flying off the southern coast of China had collided with a Chinese F-8 fighter jet. The American pilot landed safely, but the Chinese pilot was killed. China’s hackers lashed out. It wasn’t the first foreign attack on American sites, but it was the biggest — “the First World Hacker War,” as the New York Times dubbed it.
The Chinese attacks were poorly coordinated, and it’s tempting to dismiss them as harmless online vandalism. But subsequent attacks have become more serious. In the past two years, Chinese hackers have intercepted critical NASA files, breached the computer system in a sensitive Commerce Department bureau, and launched assaults on the Save Darfur Coalition, pro-Tibet groups and CNN. And those are just the attacks that have been publicly acknowledged. Were these initiated by the Chinese government? Who is doing this?

Xiao Tian
Early clues came through the boasts of a single Chinese hacker. On May 20, 2003, a man named Peng Yinan, then known only by the moniker coolswallow, logged into a public Shanghai Jiaotong University student forum and described how he formed a group at the university’s Information Security Engineering School that coordinated with other hackers to bring down whitehouse.gov in 2001. “Javaphile was established by coolswallow (that’s me)” and a partner, he wrote in Chinese. “At first we weren’t a hacker organization. After the 2001 China-U.S. plane collision incident, Chinese hackers declared an anti-American Battle . . . and coolswallow joined in the DDoS White House attacks.” Later, he bragged, his group defaced other sites it considered anti-Chinese, including that of the Taiwanese Internet company Lite-On.
Peng left two e-mail addresses, his chat information and the screen names of four other hackers. He soon expanded his online profile with a blog, photos, and papers describing his hacking openly. But his boasts went unnoticed until 2005, when a linguist in Kansas typed the right words into Google, found Peng, and pulled back the curtain on a growing danger.

Goodwell
GHOSTS IN THE MACHINE
In its report to Congress last year, the U.S.-China Economic and Security Review Commission called Chinese cyber-espionage a major threat to U.S. technology. “China is aggressively pursuing cyber warfare capabilities that may provide it with an asymmetric advantage against the United States,” the commission warned. As everything from health-care services to credit-card records to classified military information moves into a networked age, the risk that our digital systems could be crippled by outside attackers — or worse, pillaged for sensitive information — is very real. The commission report cited vulnerable American targets such as the electric grid and the municipal-waste, air-traffic-control, banking and Social Security systems. Before leaving office in January, President Bush authorized the creation of a National Cyber Security Center under the Department of Homeland Security, and in February, President Obama’s budget proposal called for giving the department $355 million to secure private- and public-sector cyber-infrastructure.
But there’s reason to believe that a damaging attack won’t originate in some dedicated Chinese government bureau. In previous testimony before the commission, James C. Mulvenon, director of the defense think tank the Center for Intelligence Research and Analysis, said he was more immediately concerned with independent, civilian-led “patriotic hacking.”
James Andrew Lewis, a senior fellow at the Center for Strategic and International Studies (CSIS), which helped develop cybersecurity policy recommendations for the Obama administration, shares that concern. “The U.S. government had a number of serious computer incidents in 2007, most of which were attributed to China,” he says. “The focus in Washington is on what appear to be state-sponsored activities. That, of course, is only a part of what’s going on in China.”
From China, where I’ve lived for four years, this assessment looks spot-on. Hackers are pervasive, their imprint inescapable. There are hacker magazines, hacker clubs and hacker online serials. A 2005 Shanghai Academy of Social Sciences survey equates hackers and rock stars, with nearly 43 percent of elementary-school students saying they “adore” China’s hackers. One third say they want to be one. This culture thrives on a viral, Internet-driven nationalism. The post-Tiananmen generation has known little hardship, so rather than pushing for democracy, many young people define themselves in opposition to the West. China’s Internet patriots, who call themselves “red hackers,” may not be acting on direct behalf of their government, but the effect is much the same.

Scott Henderson
STUMBLING ONTO THE DANGER
In 2004, Scott Henderson, a trim 46-year-old with sandy brown hair, had just retired from decades as a language expert for the U.S. Army to work for a private intelligence contractor in Fort Leavenworth, Kansas. With a command of Mandarin, not to mention a Taiwanese wife, Henderson’s knowledge of China makes him valuable in the intelligence community. His mandate at the new job was open-source intelligence, which meant using only information from publicly available sources, mimicking the capabilities of the average civilian. Although he had little experience in the subject, he was assigned a report on Chinese hackers.
Sitting down at a desk overlooking the Fort Leavenworth military base, Henderson started, like any novice, with Google. Using Mandarin characters, he typed heike — literally, “black guest” — pulling up the characters for “hacker.” Probably, he thought, he’d find articles rehashing weak Western reports. But when he hit “return,” his browser displayed a slew of unfamiliar sites: hackbase.com, hacker123.com, hack8.cn. There were hundreds, maybe thousands. He quickly realized that each was the online headquarters of a Chinese hacker organization, with detailed logs of hacks, contact information for hackers, and forums where users discussed targets. Chinese hackers, it turns out, take credit on their own sites for attacks, leaving a long trail of documentation. They are so attention-driven that when they post images of their successes to online trophy rooms, they tag them with e-mail addresses, URLs, even cellphone numbers. Within three minutes, Henderson had more information than he knew what to do with.
He spent the next few months trying to make sense of the data. To map connections among hacker sites, he laid a large sheet of paper out on the floor of his office and started sketching the network by hand. The diagram quickly extended off the page. Then it extended off several taped-together pages. After a co-worker suggested the computer program i2 Analyst’s Notebook, an investigative tool that allowed him to craft a more sophisticated model, Henderson, following links from site to site, connected 250 hacker pages. Monitoring a cross-section of sites over several days to estimate the number of people logged in at any given time, he came up with 380,000 hackers.
There were localized clubs, whose members saw one another regularly. There were fleeting groups, whose sites appeared and disappeared in a matter of weeks. There were kid hackers, femme-fatale hackers and hacker wannabes (although most hackers are simply computer-savvy 20-somethings — what Henderson calls “normal guys”). One group penned a theme song. Henderson recognized early on that such publicity ploys were not the work of the state. “If this was some secret government-run organization,” he says, “it was the most horribly run secret government organization in the universe.”
Instead, Chinese hackers work in small, competing crews, he found. During moments of crisis, like the 2001 EP-3 collision, the groups band together into coalitions called “Chinese emergency conference centers.” The Red Hacker Alliance, often described in the Western press as a monolithic group, is in fact a loose association allowing disparate cells to coordinate their efforts.
But the largest unifying characteristic is nationalism. In a 2005 Hong Kong Sunday Morning Post article, a man identified as “the Godfather of hackers” explains, “Unlike our Western [hacker] counterparts, most of whom are individualists or anarchists, Chinese hackers tend to get more involved with politics because most of them are young, passionate, and patriotic.” Nationalism is hip, and hackers — who spearhead nationalist campaigns with just a laptop and an Internet connection — are figures to revere.
Henderson says he’s found nothing to show a direct connection between the central government and civilian hacker groups. But he emphasizes that the relationship between citizen and state is fluid in China, and that the Chinese government tends not to prosecute hackers unless they attack within China. To Henderson, that lack of supervision is tacit approval, and it constitutes a de facto partnership between civilian hackers and the Chinese government.
Jack Linchuan Qiu, a communications professor at the Chinese University of Hong Kong who spent the 2001 hacker war logged into mainland forums, agrees. “Chinese hackerism is not the American ‘hacktivism’ that wants social change,” he says. “It’s actually very close to the state. The Chinese distinction between the private and public domains is very small.” Chinese entrepreneurs returning from working in Silicon Valley, Qiu says, sometimes comply with government requests to provide filtering technology to China’s Internet police. Homegrown hackers might just as easily be recruited to write viruses or software for the People’s Liberation Army.
Ultimately, hackers with loose government connections may be more frightening than state-sponsored cyberwarfare. According to Lewis, “The government at a minimum tolerates them. Sometimes it encourages them. And sometimes it tasks them and controls them.” In the end, he says, “it’s easy for the government to turn on and hard to turn off.”
“These rogue groups are missing oversight,” Henderson says. “When a situation is approaching critical mass” — if, for instance, these hackers decide to abandon simple vandalism and start gunning for Social Security numbers or classified information — “who’s the guy who pulls back and says, ‘No, we don’t go any further’?”

Faces in the Crowd
A HACKER IS BORN
Shanghai Jiaotong University, one of the best in China, sits on the southern edge of Shanghai, surrounded by the R&D labs of multinational corporations. On the day I visit, students are sprawled on a verdant lawn, chatting and studying. Just behind them is the Information Security Engineering School, a futuristic mélange of maroon and gray.
Peng Yinan formed Javaphile here in September 2000. Peng originally saw the group as a way to explore physics and programming. But the following spring, patriotic fury at the EP-3 collision turned the group to hacking. A scholarship student, Peng was dark and intense, with long bangs hanging over his eyes and a fondness for horror films, Buddhist texts, and blogging about food. A former roommate of Peng’s tells me his anti-American sentiments were common. “Everybody was very nationalistic,” he says. “It’s not like he was exceptional.”
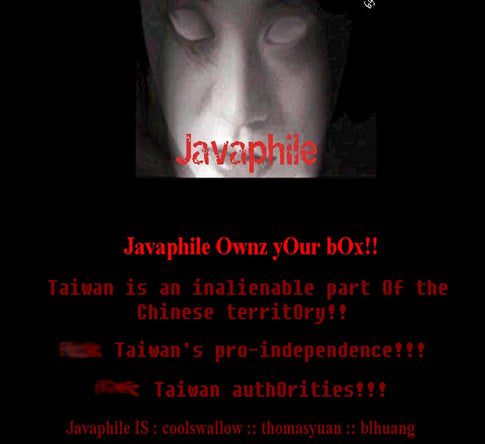
In 2002, Peng and two other hackers broke into the Web site of Lite-On and replaced the Taiwanese firm’s home page with an image of a white face with hollowed-out eyes, along with the message “[F-ck] Taiwan’s pro-independence!!!” In December 2003, the ghost face reemerged on the U.S. Navy Chartroom site, an internal Navy page. “[F-ck] usa.gov,” read the defacement, which was signed by coolswallow and four others.
Soon after, Javaphile disintegrated. But Peng continued to take online casualties, defining his role as electronic patriot more and more broadly. After the U.S. invasion of Iraq in 2003, Peng, objecting to American imperialism, plastered the Washington, D.C. — area Fox News site with “Allah Bless Iraq!!! Don’t throw bombs, throw Bush.”
CHASING PENG
In 2006 Henderson published a book about his search for Chinese hackers, The Dark Visitor, and in November 2007 he posted a profile of Javaphile to his blog, thedarkvisitor.com. He didn’t yet know coolswallow’s real name, so he used the hacker’s screen handle, which was easy to deduce from Javaphile forum posts. Hackers regularly read Henderson’s blog; once, one e-mailed to complain that government censors had blocked the site. So when traffic spiked a few weeks after the Javaphile post, Henderson checked to see where it was coming from.

Withered Rose
He traced the traffic to a Jiaotong University forum, where a user named ericool had linked to Henderson’s site. “There’s a passage about Javaphile and coolswallow,” ericool wrote. “He uses my blog.” Henderson soon pulled up posts connecting ericool to a Jiaotong University group called Pneuma, along with a post from 2002 that ericool had signed “CoolSwallow of Javaphile.” They were the same person.
Clicking through the discussion schedule on Pneuma’s Web site, pneuma.cn (devoted to “cherishing the motherland when gazing at the world”), Henderson learned that a “senior hacker” named Peng Yinan had delivered Pneuma’s second-anniversary lecture, “Hacker in a Nutshell.” The poster for the event was appended with a quote from Hamlet: “I could be bounded in a nutshell and count myself a king of infinite space.”
One PowerPoint slide from the lecture underlines the importance of simple, openly available techniques, noting that in 2006 the Chicago Tribune obtained contact information for 2,600 CIA agents using a commercial online service and suggesting that hackers “use illegal methods in weak sites to obtain information on personnel from safe sites.” Chinese coverage of the event showed Peng lecturing easily from behind an open laptop. Henderson now had definitive evidence connecting coolswallow and ericool to Peng’s name, allowing him to reconstruct the hacker’s biography. What most intrigued him, however, was a phrase in small type at the bottom of the Pneuma flyer describing Peng as a consultant for the Shanghai Municipal Bureau of Public Security.
Henderson promptly posted his findings on his blog, with a copy of the presentation, an introduction to Pneuma, and Peng Yinan’s photo. It was impossible to deduce the exact nature of Peng’s new job. Based on the flyer, he was working for the Shanghai government, not for the national intelligence service. But such an arrangement supported Henderson’s assessment of China’s informal government-hacker relationship, providing evidence that after hackers cut their teeth on nationalist campaigns, the government might hire them to take on freelance work.
Five hours after the post went up, a user calling himself Pneuma Collegium posted a comment: “Your use of the logo and the photo of Pneuma Collegium is . . . an infringement of Pneuma Collegium’s copyright.” When Henderson saw that the poster’s IP address belonged to pneuma.cn, his blood boiled. Henderson removed the logo and the PowerPoint presentation but kept the photo up, citing U.S. law on fair use of images. His aim, he told me later, was to keep the image of Peng publicly available. “When the FBI gets their hands on you,” he said, as if still in conversation with the hacker, “I want them to match this picture to your face — and take you to jail.”

Chinese Attack on a Taiwanese Manufacturer’s Site
WHEN WILL WE CATCH ON?
The problem, of course, is that it’s practically impossible for the FBI to catch or prosecute hackers operating abroad. “The international legal framework doesn’t exist,” says the CSIS’s Lewis. And extraditing a hacker to the U.S. simply doesn’t happen, given our current relationship with China. Learning to defend ourselves seems to be the only option.
In the meantime, Chinese hackers are becoming harder to monitor. Increasingly, they coordinate through private text-messaging rather than on blogs or Web sites, leaving no public record of their activities. In late 2007, after finding the Javaphile profile on Henderson’s blog, Peng logged into the Jiaotong University forum and typed, “Looks like I should quit the historical stage.” A few weeks later, he stopped posting on public forums altogether. He graduated the next month.
Last summer, I e-mailed Peng at nine e-mail addresses collected from his blog, academic papers, hacks and the Pneuma site. Eventually I received a reply from a Pneuma member called janeadios. “Peng Yinan is no longer involved with Internet security,” it read. But traces of him remained. Earlier that year, in March, he was one of three graduates invited back by the Information Security Engineering School to deliver a career talk to students.
Rather than quit hacking, Henderson speculates, Peng retreated from view. In the months leading up to the Beijing Olympics, the Chinese government tightened its control on information. Peng may have been contracted to monitor the Web. In any case, his disappearance from the virtual realm means the loss of valuable indicators of future attacks.
In February, President Obama launched a 60-day investigation into cybersecurity, pledging to improve U.S. Internet defense. Acting on the review commission’s findings, however, will require a coordinated, interdepartmental effort. First on the list should be reading Henderson’s painstakingly detailed reports. And Peng’s disappearance suggests that time is running out. If we can’t handle the information Chinese hackers are leaving now, scarier still is what could happen when it disappears.
Mara Hvistendahl also writes for the New Republic, Harper’s and Science. She lives in Shanghai.